Table of Contents
- Secure API Management with Revecast Connect
- Data Encryption
- Access Control and Identity Management
- Monitoring & Auditing
- Error Handling & Validation
- Regular Updates and Patch Management
- Secure Development Process
- Customer Responsibilites
At Revecast Connect, we deeply care about your success and are committed to supporting you with the highest standards of data security. We understand the importance of keeping your data safe and secure, and we’re here to provide you with the best practices to ensure your Salesforce integrations are robust and secure. Here are some essential tips to help you build secure integrations between Salesforce and Revecast Connect.
Secure API Management with Revecast Connect
Use Strong Authentication
- OAuth 2.0: Use OAuth 2.0 for secure and reliable authentication. This method provides token-based authentication, reducing the risk of exposing sensitive credentials.
- API Keys: Use unique API keys for different services and rotate them regularly to minimize security risks.
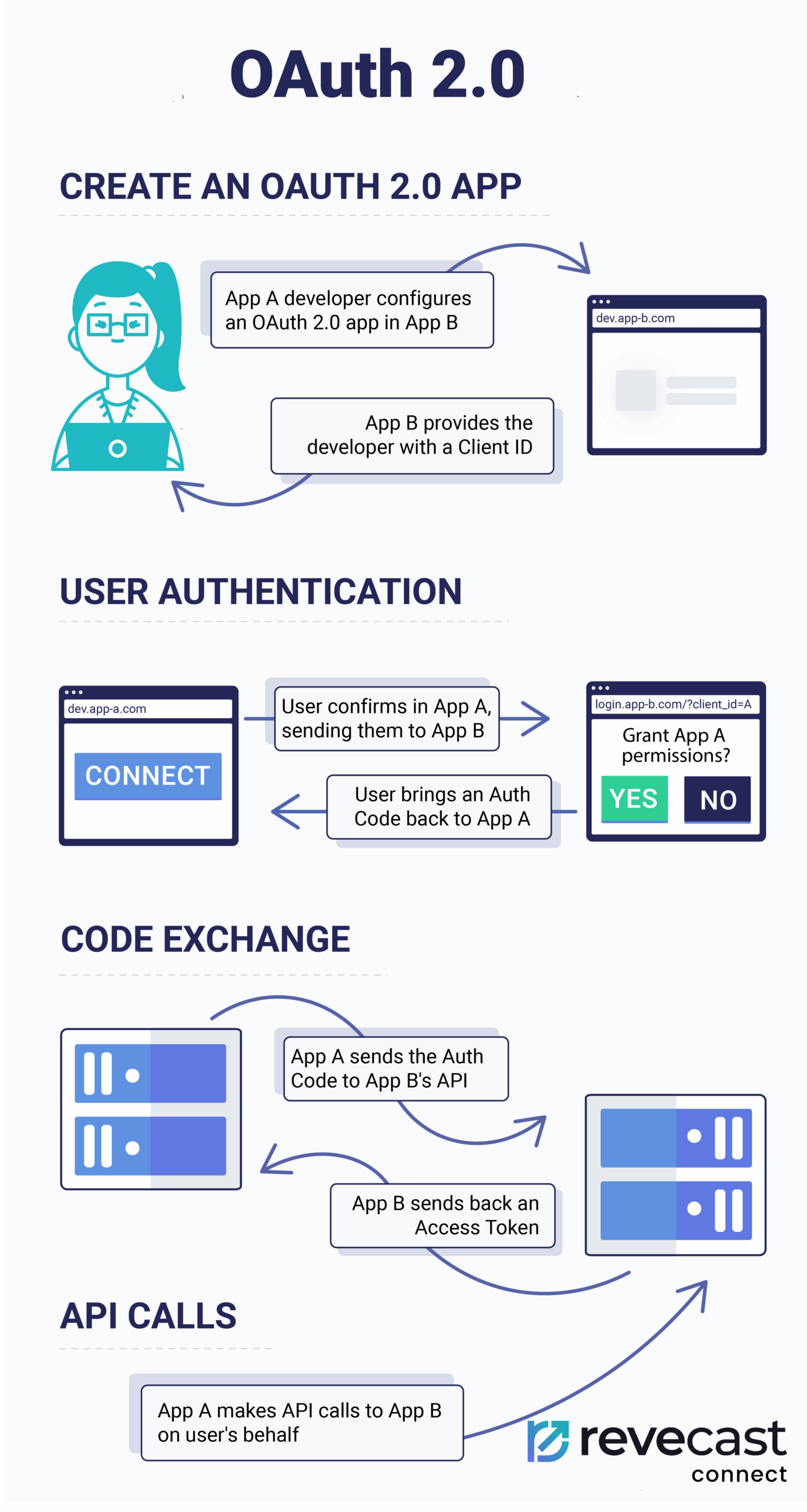
Limit API Permissions
- Least Privilege Principle: Grant only the necessary permissions required for the integration to function. Avoid using overly broad permissions that could expose sensitive data.
- Scope Definition: Clearly define and limit the scope of access for each API to ensure that only necessary data and functions are accessible.
Data Encryption
Encrypt Data In-Transit
- SSL/TLS: Use SSL/TLS encryption to protect data as it travels between Salesforce, Revecast Connect, and other integrated systems. This ensures that data remains confidential and secure during transmission.
- Encrypted Connections: Always use encrypted connections (HTTPS) for API calls and data exchanges.
Encrypt Data At-Rest
- Database Encryption: Ensure that data stored within both Revecast Connect and Salesforce is encrypted at rest using strong encryption methods.
- Field-Level Encryption: For highly sensitive data, consider using field-level encryption within Salesforce to provide an additional layer of security.
Access Control and Identity Management
Role-Based Access Control (RBAC)
- Granular Permissions: Implement RBAC to assign specific permissions based on user roles in all systems. This helps in controlling who can access and manipulate data when creating Salesforce integrations.
- User Profiles: Use user profiels to manage permissions more efficiently and ensure that access is granted based on the user’s role and responsibilities.
Multi-Factor Authentication (MFA)
- Enable MFA: Require multi-factor authentication for accessing Salesforce, Revecast Connect, and any other system you integrate. This adds an additional layer of security by requiring users to provide two or more verification factors.
Monitoring & Auditing
Activity Logging
- Comprehensive Logs: Maintain detailed logs of all integration activities, including API calls, data transfers, and user actions. This helps in monitoring for suspicious activities and auditing compliance.
- Log Management: Use centralized log management systems to aggregate and analyze logs from Salesforce and Revecast Connect.
Regular Audits
- Security Audits: Conduct regular security audits of your integrations to identify and address potential vulnerabilities.
- Compliance Checks: Ensure that your integrations comply with relevant regulatory requirements and industry standards.
Error Handling & Validation
Robust Error Handling
- Graceful Failures: Implement robust error handling to manage integration failures gracefully and securely.
- Error Logging: Log errors in a secure and controlled manner without exposing sensitive information.
Data Validation
- Input Validation: Validate all input data to prevent SQL injection, cross-site scripting (XSS), and other common security vulnerabilities.
- Output Encoding: Encode output data to ensure that it is rendered safely in user interfaces.
Regular Updates and Patch Management
Stay Updated
- Software Updates: Regularly update Revecast Connect, Salesforce, and any other integrated systems to the latest versions to benefit from security patches and improvements.
- Dependency Management: Keep all third-party libraries and dependencies up to date to mitigate known vulnerabilities.
Patch Management
- Timely Patching: Apply security patches promptly to minimize exposure to potential threats.
- Automated Updates: Where possible, use automated tools to manage updates and patches.
Secure Development Process
Code Reviews
- Peer Reviews: Conduct peer code reviews to identify and fix security issues during the development process.
- Automated Scanning: Use automated security scanning tools to detect vulnerabilities in your codebase.
Secure Coding Standards
- Best Practices: Follow secure coding best practices and guidelines to prevent common vulnerabilities.
- Training: Ensure that your development team is trained in secure coding techniques and aware of the latest security threats.
Customer Responsibilites
Secure Configuration
- Follow Guidelines: Adhere to the recommended configuration guidelines provided by Revecast Connect, Salesforce, and all other integration tools to ensure secure setup and integration.
- Environment Separation: Use separate environments for development, testing, and production to prevent accidental data exposure and ensure a controlled release process.
User Education
- Security Training: Provide regular security training for users to help them understand best practices for data protection and threat mitigation.
- Access Management: Regularly review and update user access permissions to ensure they are current and aligned with their job roles.
Incident Reporting
- Report Issues Promptly: Encourage users to report any security incidents or suspicious activities immediately. Provide clear instructions on how to report issues to your IT or security team.
- Collaboration: Work closely with all vendors to address and resolve any security concerns quickly and effectively.
At Revecast Connect, we care deeply about our customers and are dedicated to supporting you with safe and secure data practices. By following these best practices, you can build secure integrations between Salesforce and Revecast Connect, protecting your data and maintaining the integrity of your systems. If you have any questions or need further assistance, our support team is here to help.
Thank you for choosing Revecast Connect. Your security is our priority!









